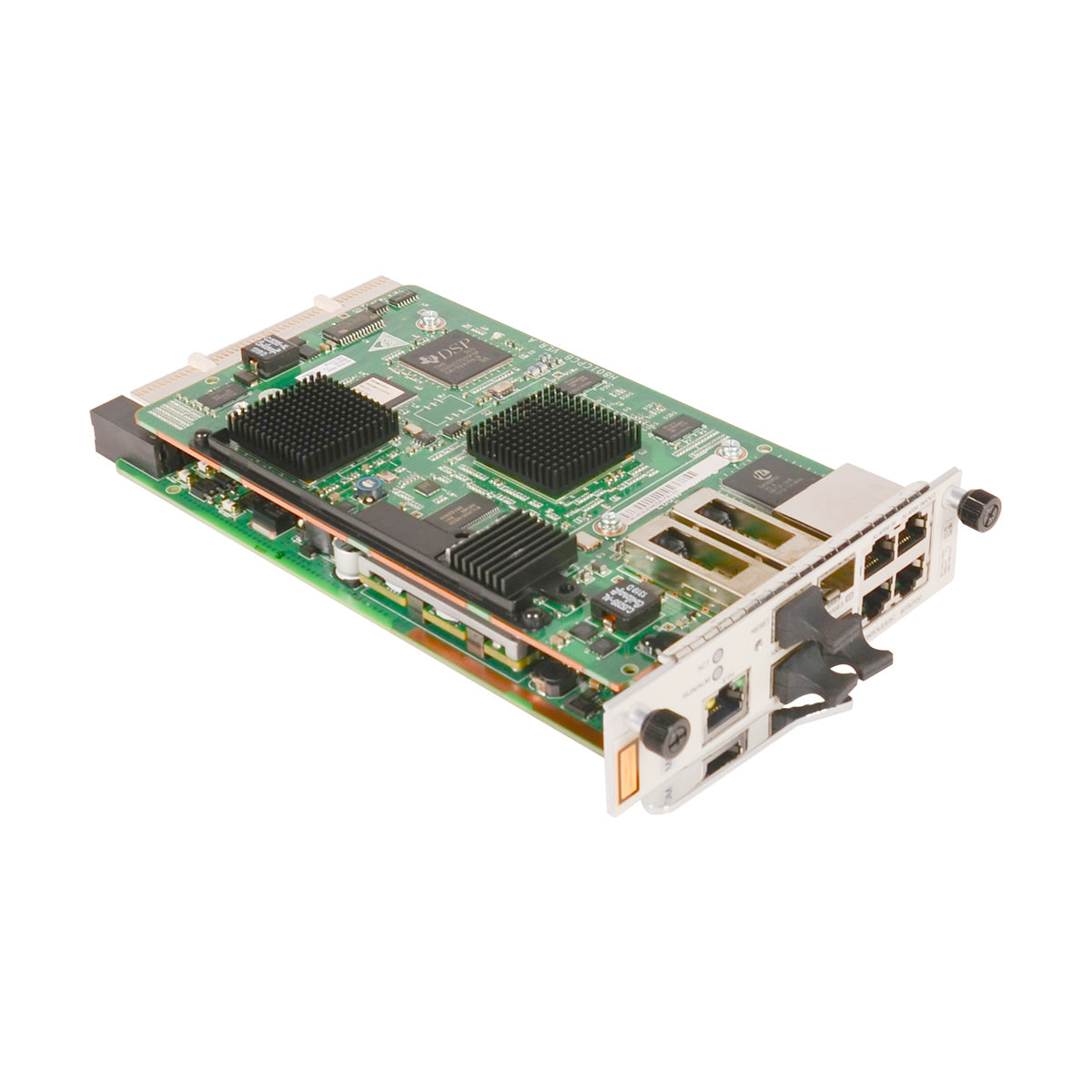
Huawei S5720-56C-EI-AC switch with 48-ports 1000BASE-T, 4-ports 10GE SFP+, 2 power slots
With 1 extension slot
Forwarding performance: 162 Mpps
Switching capacity: 598Gbps
64K MAC address entries
Huawei S5720-EI series provide flexible all-gigabit access and enhanced 10 GE uplink port scalability. They are widely used as access/aggregation switches in enterprise campus networks or gigabit access switches in data centers.
| Item | Description |
| Fixed port | 48×10/100/1000Base-T Ethernet ports and 4x10G SFP+ ports |
| Forwarding performance | 162 Mpps |
| Extended slot | One extended slot that supports an uplink interface card or private stack card |
| DRAM and Flash | SDRAM: 2 GB; Flash: 340 MB |
| MAC address table | IEEE 802.1d |
| 64K MAC address entries | |
| MAC address learning and aging | |
| Static, dynamic, and blackhole MAC address entries | |
| Packet filtering based on source MAC addresses | |
| VLAN | 4K VLANs |
| Guest VLAN and voice VLAN | |
| GVRP | |
| MUX VLAN | |
| VLAN assignment based on MAC addresses, protocols, IP subnets, policies, and ports | |
| 1:1 and N:1 VLAN mapping | |
| VLAN-based transparent transmission of protocol packets | |
| Jumbo frame | 12K |
| Ring protection | RRPP ring topology and RRPP multi-instance |
| Smart Link tree topology and Smart Link multi-instance, providing millisecond-level protection switchover |
|
| Smart Ethernet Protection (SEP),G.8032 Ethernet Ring Protection Switching (ERPS) | |
| STP (IEEE 802.1d), RSTP (IEEE 802.1w), and MSTP (IEEE 802.1s) | |
| BPDU protection, root protection, and loop protection; BPDU tunnel | |
| IP routing | Static routing, RIPv1/2, RIPng, OSPF, OSPFv3, IS-IS, IS-ISv6, BGP, BGP4+, ECMP, and policy-based routing |
| 16K IPv4 unicast routes, 8K IPv6 unicast routes | |
| 3K IPv4 static routes, 1K IPv6 static routes | |
| IPv6 features | Neighbor Discovery (ND) |
| Path maximum transmission unit (PMTU) | |
| IPv6 Ping, IPv6 Tracert, and IPv6 Telnet | |
| 6 to4 tunnel, ISATAP tunnel, and manually configured tunnel | |
| ACLs based on source IPv6 addresses, destination IPv6 addresses, Layer 4 ports, or protocol types |
|
| Multicast Listener Discovery (MLD) v1/v2 snooping | |
| Multicast forwarding | IGMP v1/v2/v3 snooping and IGMP fast leave |
| Multicast forwarding in a VLAN and multicast replication between VLANs | |
| Multicast load splitting among trunk member ports | |
| Controllable multicast | |
| Layer 2 multicast control | |
| Port-based multicast traffic statistics collection | |
| IGMPv1/v2/v3, Protocol Independent Multicast Sparse Mode (PIM-SM), and Protocol Independent | |
| Multicast Dense Mode (PIM-DM), and Protocol Independent Multicast Source-Specific Multicast (PIM-SSM) | |
| Multicast Source Discovery Protocol (MSDP) | |
| QoS/ACL | Inbound and outbound traffic rate limiting on a port |
| Packet redirection | |
| Broadcast storm control | |
| Port-based traffic policing and two-rate and three-color CAR | |
| Eight queues per port,Weighted round robin (WRR), deficit round robin (DRR), strict priority (SP), WRR+SP, and DRR+SP queue scheduling algorithms | |
| Weighted random early detection (WRED) | |
| Re-marking of the 802.1p priority and DSCP value of packets | |
| Packet filtering based on Layer 2 to Layer 4 information, including source MAC addresses, destination MAC addresses, source IP addresses, destination IP addresses, TCP/UCD source/destination ports, protocol types, and VLAN IDs | |
| Per queue rate limiting and interface traffic shaping | |
| 1:1,N:1,N:4 port mirroring; VLAN mirroring | |
| Security features |
Hierarchical user management and password protection |
| DoS attack defense, ARP attack defense, and ICMP attack defense | |
| Binding of the IP address, MAC address, interface number, and VLAN ID of a user | |
| Port isolation, port security, and sticky MAC | |
| MAC Forced Forwarding (MFF) | |
| Blackhole MAC address entries | |
| Limit on the number of learned MAC addresses | |
| IEEE 802.1x authentication and the limit on the number of users on an interface | |
| AAA authentication, RADIUS authentication, HWTACACS+ authentication, and NAC SSH v2.0 | |
| Hypertext Transfer Protocol Secure (HTTPS) | |
| CPU defense; Blacklist and whitelist; MACSec ready | |
| Access security | DHCP Relay, DHCP Server, DHCP Snooping, DHCP Client, DHCP Security |
| Port aggregation | LACP |
| Up to 128 trunk groups | |
| Up to 8 member interfaces in each trunk group | |
| Reliability | Ethernet OAM (IEEE 802.3ah and 802.1ag) |
| ITU-Y.1731; BFD for BGP/IS-IS/OSPF/static route | |
| Super Virtual Fabric (SVF) | Working as an SVF client that is plug-and-play with zero configuration |
| Automatically loading the system software package and patches of clients | |
| One-click and automatic delivery of service configurations | |
| Supports independent running client | |
| Management and Maintenance |
iStack, Virtual cable test, SNMP v1/v2c/v3, RMON/RMON2 |
| Web-based network management system | |
| System logs and multi-level alarms | |
| sFlow, LLDP/LLDP-MED, 802.3az EEE | |
| SCP (Secure Copy Protocol), TFTP, FTP | |
| Store dual software images and configuration files | |
| Interoperability | VLAN-based Spanning Tree (working with PVST/PVST+/RPVST) |
| Link-type Negotiation Protocol (LNP), similar to the Dynamic Trunking Protocol (DTP) | |
| VLAN Central Management Protocol (VCMP), similar to the VLAN Trunk Protocol (VTP) | |
| Operating environment | Operating temperature: 0-1800 m altitude: 0-45℃ 1800-5000m altitude: The operating temperature reduces by 1℃ every time the altitude increases by 220m. Relative humidity: 5% to 95% (noncondensing) |
| Input voltage | AC: Rated voltage range: 100 V to 240 V A C, 50/60 Hz Maximum voltage range: 90 to 264 V AC, 47/63 Hz |
| Dimensions (mm) | 442 (W) x 220 (D)x 43.6 (H) |
| Typical power consumption |
40.5W |
| PN. | 02359504 |